At 10-Year Milestone, Microsoft's Trustworthy Computing Initiative More Important than Ever - Stories
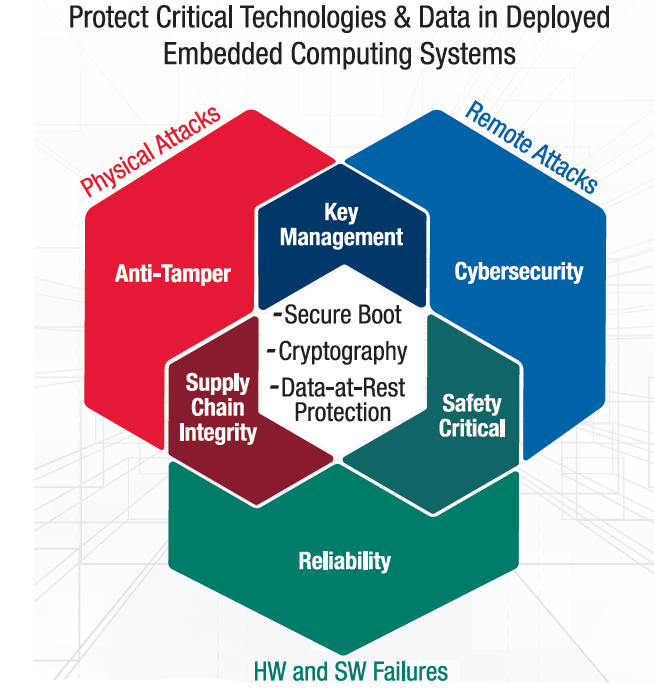
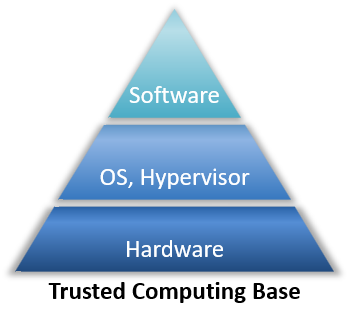
COTS-Based Trusted Computing: Getting Started in Next-Generation Mission-Critical Electronics | Curtiss-Wright Defense Solutions

Benefits of Using Trusted Computing Technology | Trusted Computing Platforms, the Next Security Solution | InformIT
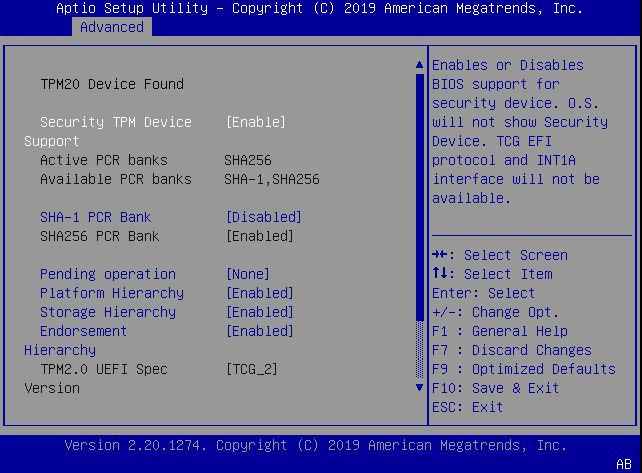
![Motherboard] Which ASUS model supports Windows 11 and how to setup TPM 2.0 in BIOS? | Official Support | ASUS Global Motherboard] Which ASUS model supports Windows 11 and how to setup TPM 2.0 in BIOS? | Official Support | ASUS Global](https://kmpic.asus.com/images/2021/07/02/2ec2cf1d-0fee-4abe-bb99-b7c1e2cd4790.png)









![Gigabyte MZ32-AR0 (rev. 1.0) [33/146] 2 1 trusted computing Gigabyte MZ32-AR0 (rev. 1.0) [33/146] 2 1 trusted computing](https://mcgrp.ru/views2/1679946/page33/bg21.png)