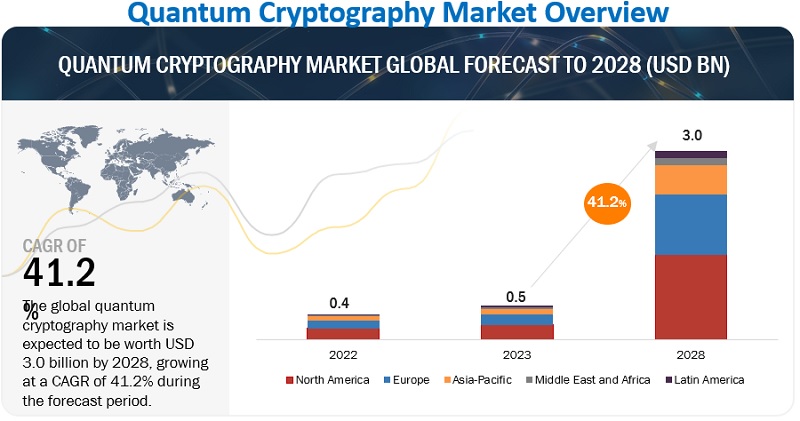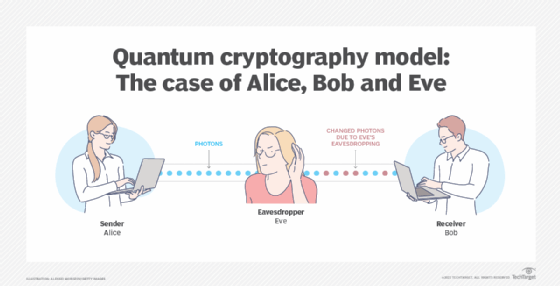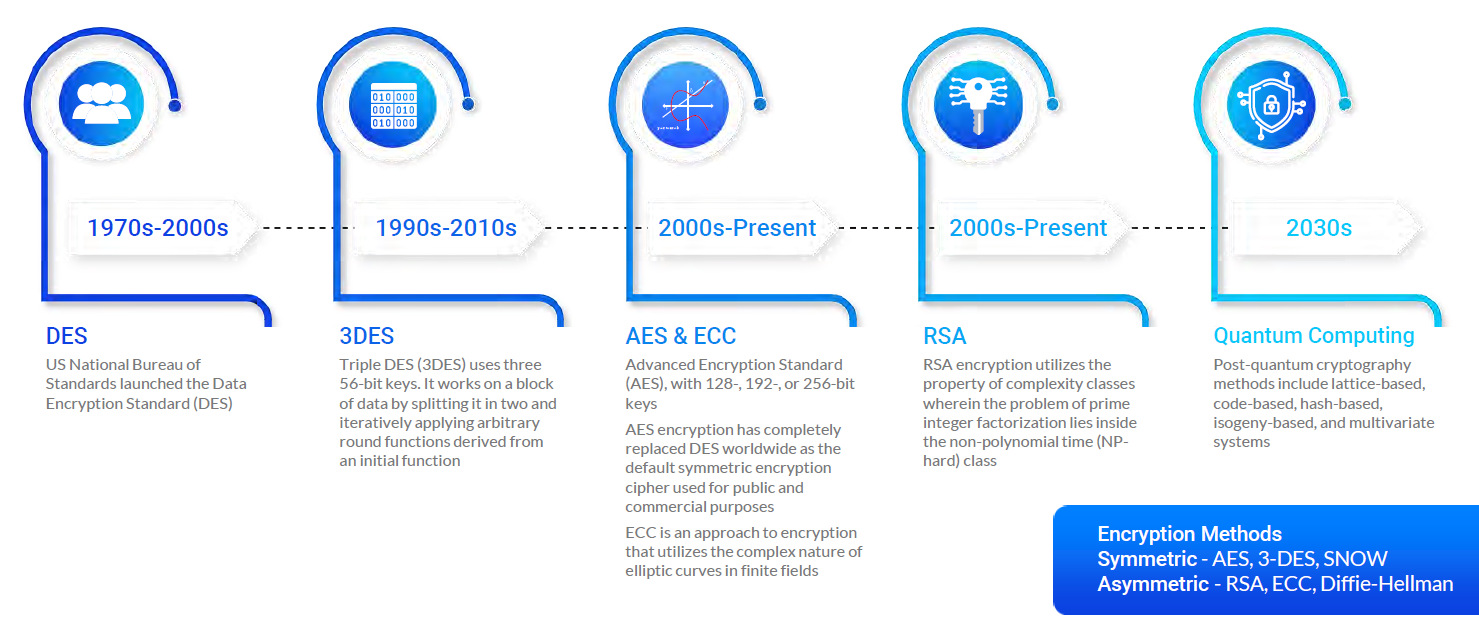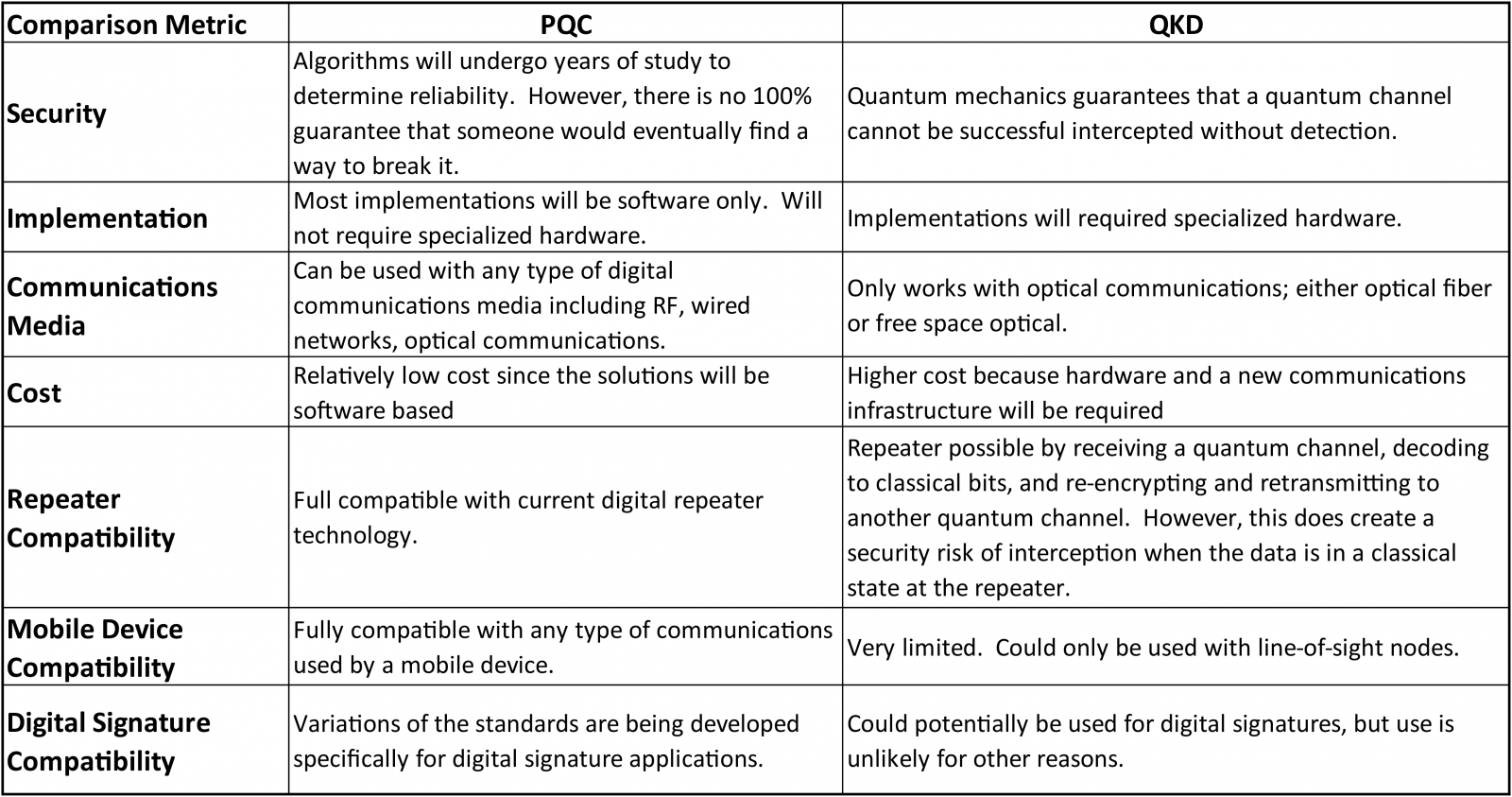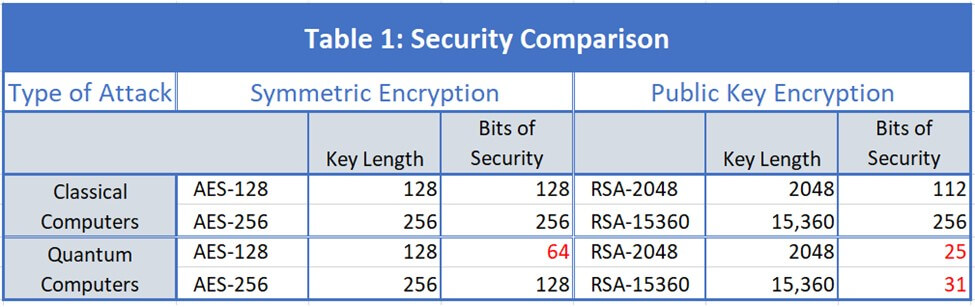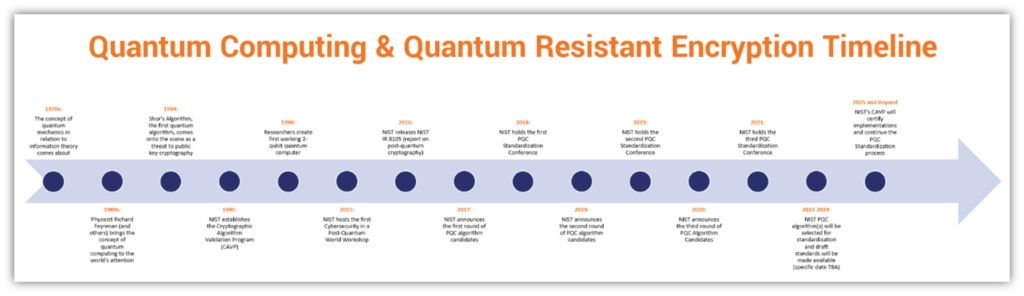
A Look at Quantum Resistant Encryption & Why It's Critical to Future Cybersecurity - Hashed Out by The SSL Store™
Post-Quantum Cryptography: A Look At How To Withstand Quantum Computer Cyber Attacks - CB Insights Research
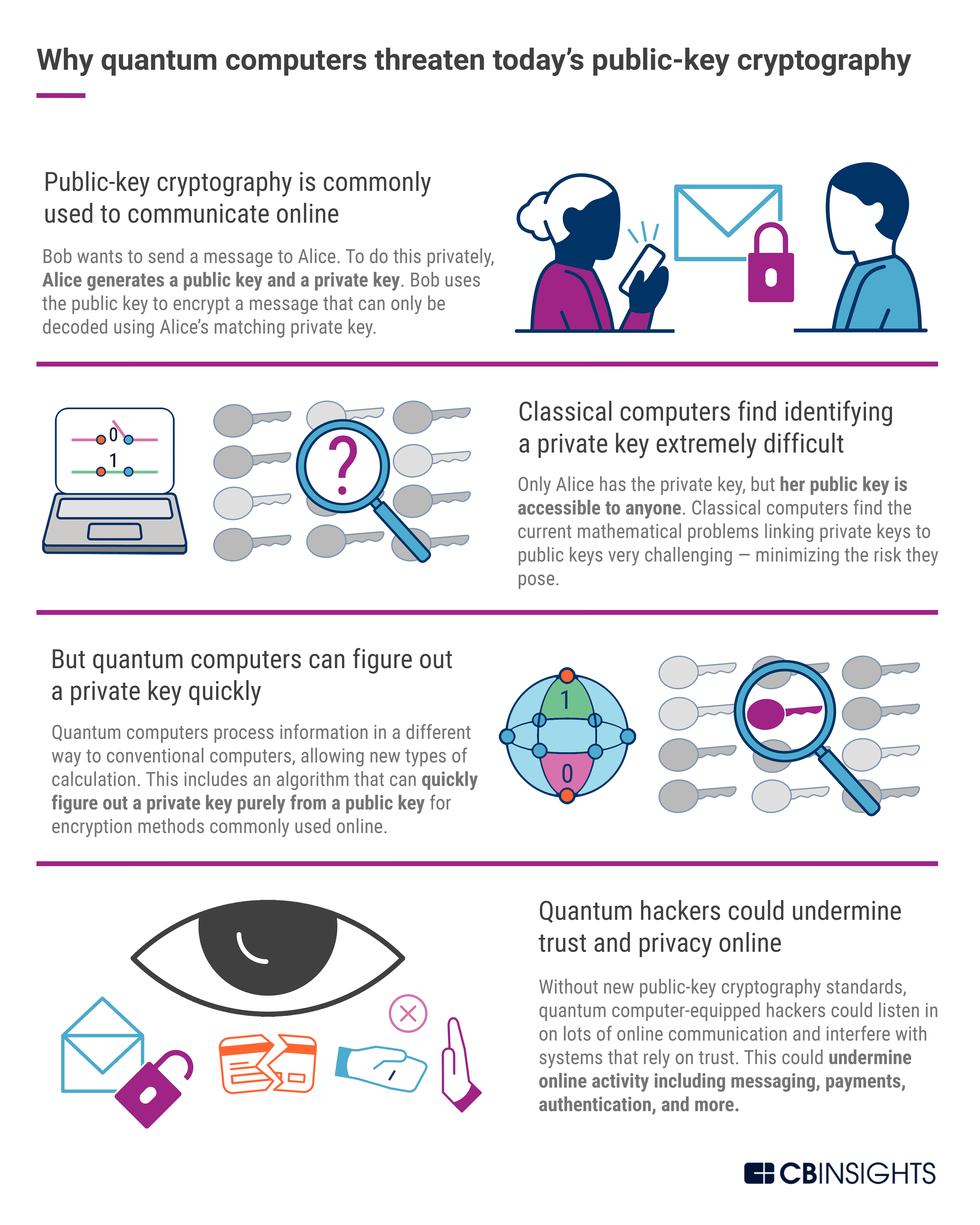
Post-Quantum Cryptography: A Look At How To Withstand Quantum Computer Cyber Attacks - CB Insights Research

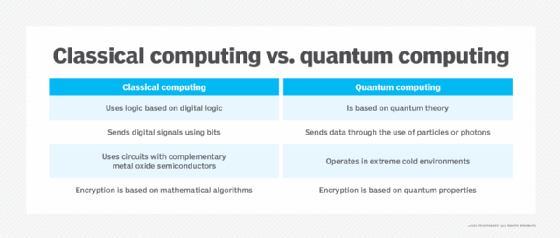
Quantum computing will break today's encryption standards - here's what to do about it | About Verizon



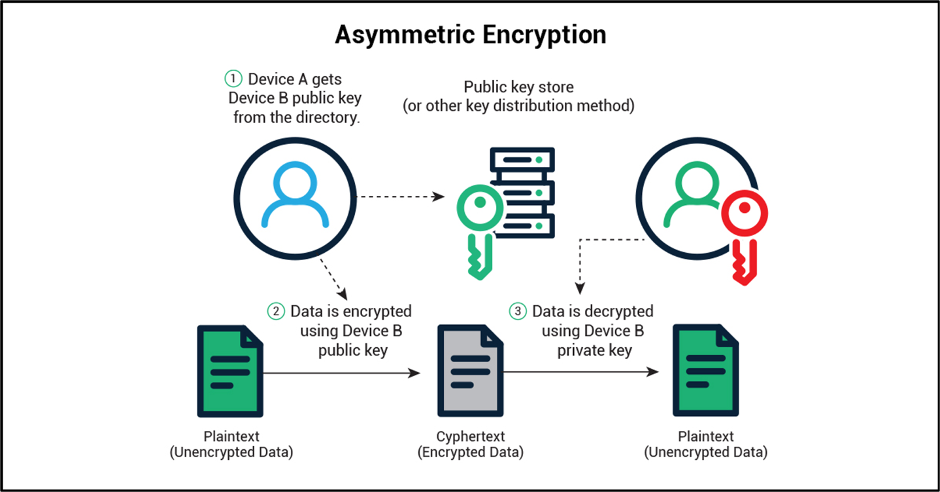
![PDF] The Impact of Quantum Computing on Present Cryptography | Semantic Scholar PDF] The Impact of Quantum Computing on Present Cryptography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/67b1d6f02e8b1c7c46513790a4132c5248a1f51f/7-Figure1-1.png)