
Trusted Path and Trusted Channel by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
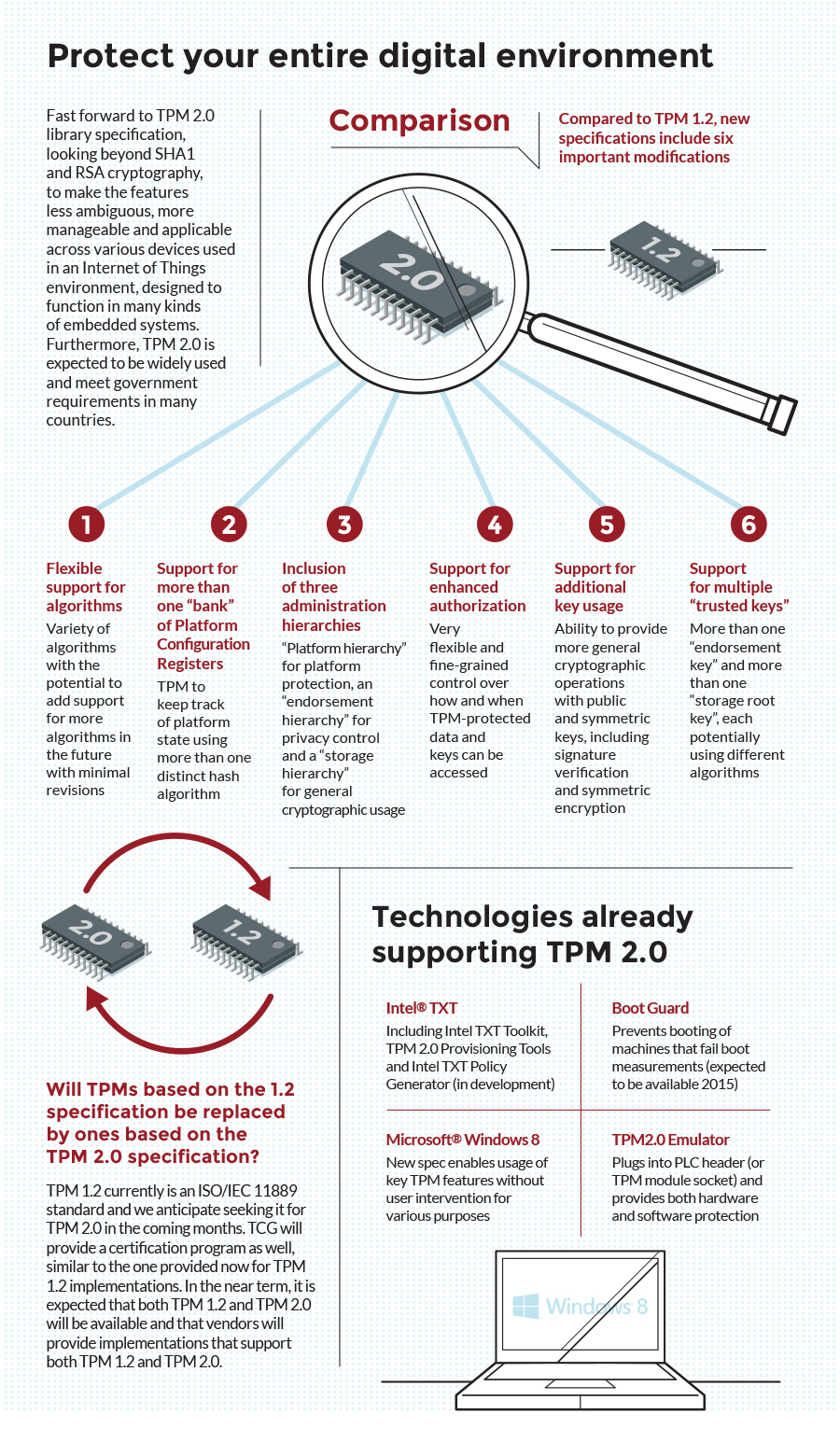
Riassunto: Trusted Computing Group lancia la specifica TPM 2.0 per accrescere la sicurezza di dispositivi e piattaforme | Business Wire
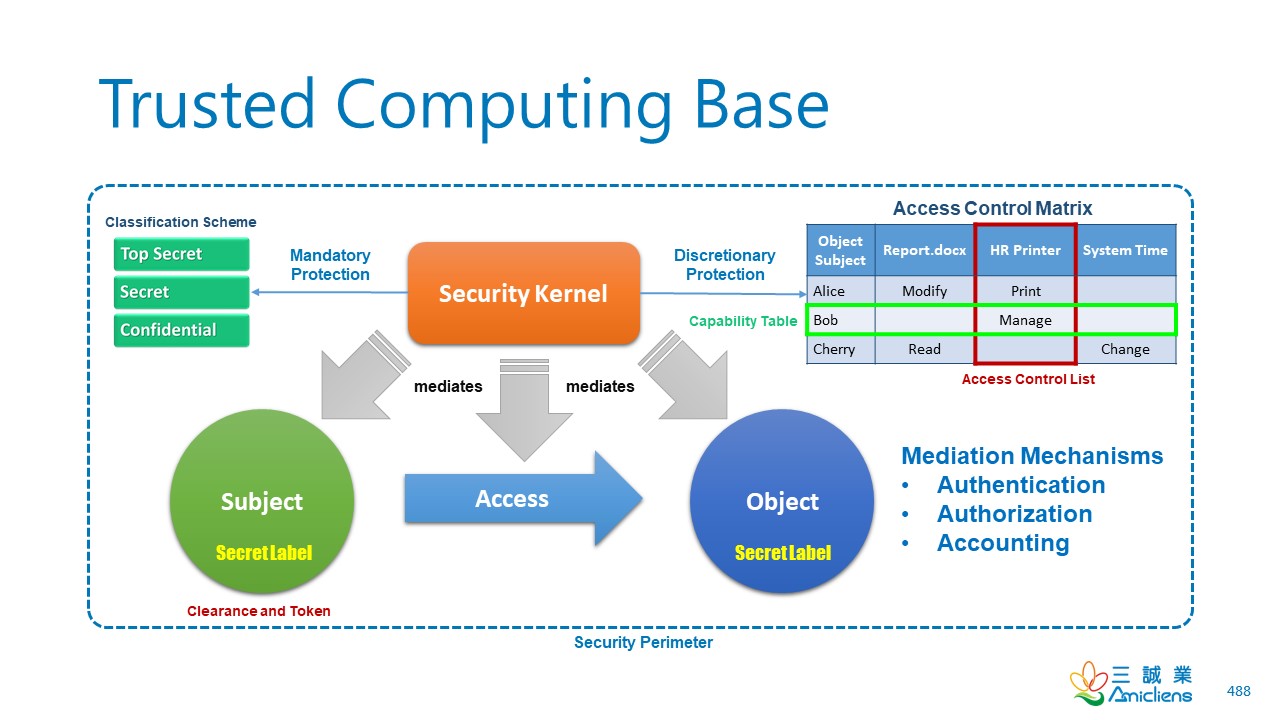
CISSP PRACTICE QUESTIONS – 20190822 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Process-Oriented Trust Framework When the Trusted Computing Group's... | Download Scientific Diagram

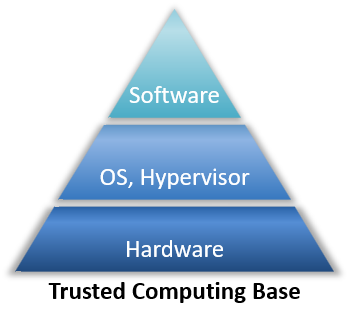
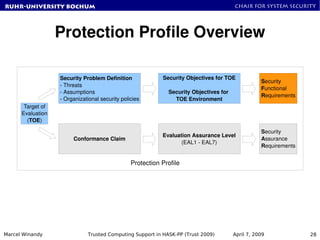
Modeling Trusted Computing Support in a Protection Profile for High Assurance Security Kernels | SpringerLink

At 10-Year Milestone, Microsoft's Trustworthy Computing Initiative More Important than Ever - Stories
COTS-Based Trusted Computing: Getting Started in Next-Generation Mission-Critical Electronics | Curtiss-Wright Defense Solutions
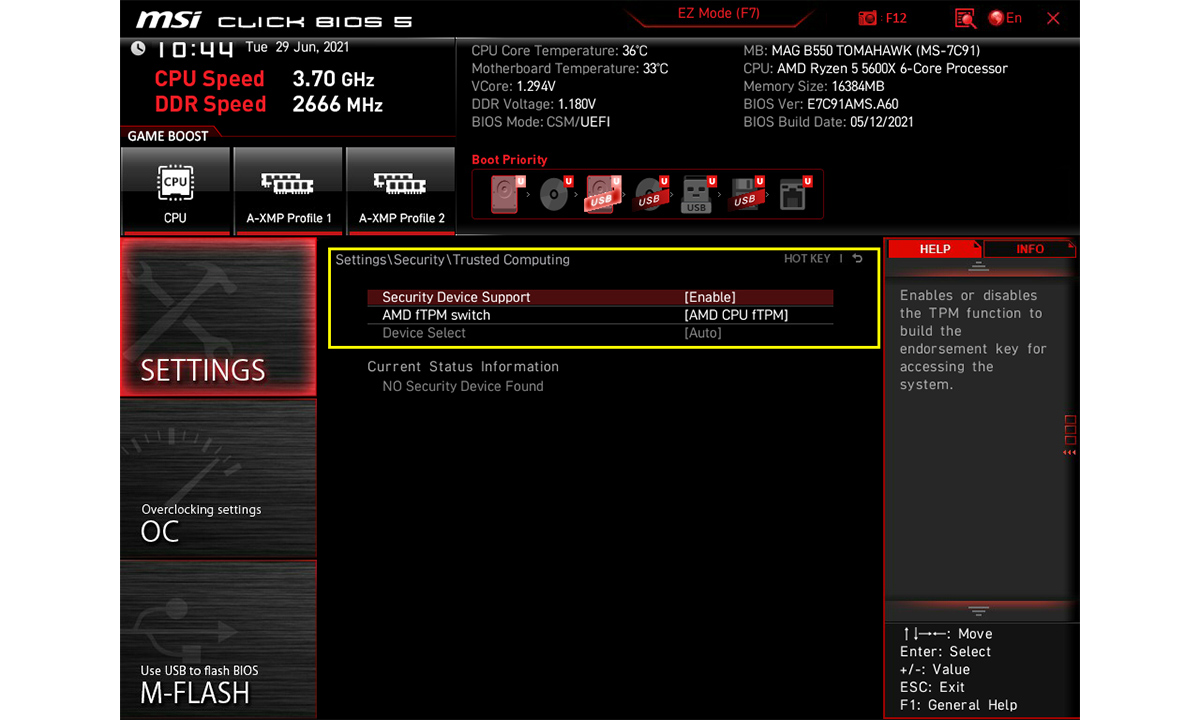
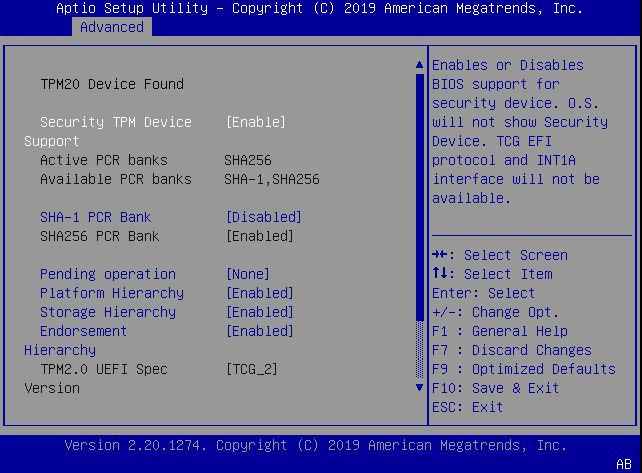
![Motherboard]How to disable TPM when update to BIOS version default support Windows 11 | Official Support | ASUS Global Motherboard]How to disable TPM when update to BIOS version default support Windows 11 | Official Support | ASUS Global](https://kmpic.asus.com/images/2022/01/27/28e31a73-d823-4ba0-881e-1cbbaa3515c8.jpg)

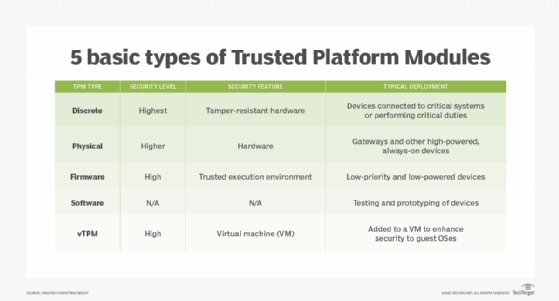

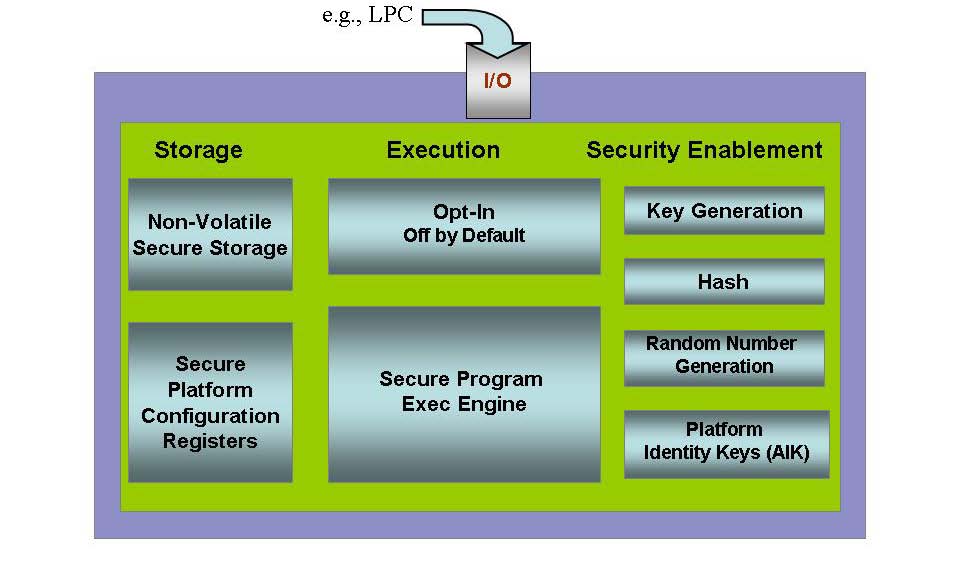









![PDF] Trusted Computing Platforms , the Next Security Solution | Semantic Scholar PDF] Trusted Computing Platforms , the Next Security Solution | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4a82f9c66e39b1335bdc8fa3eb0880e9a0370446/7-Figure1-1.png)