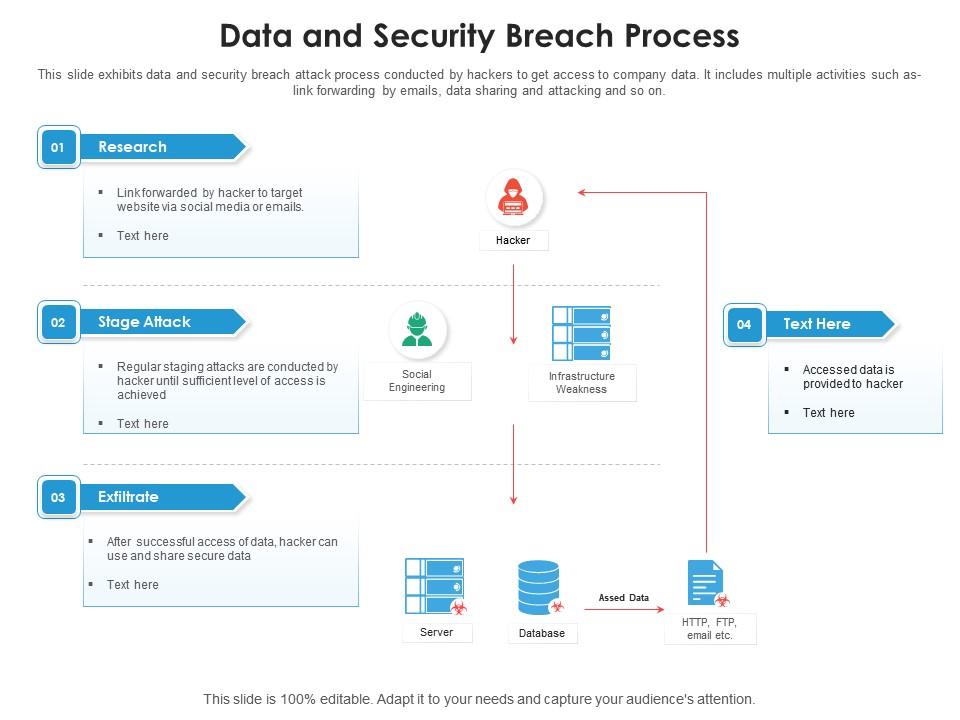
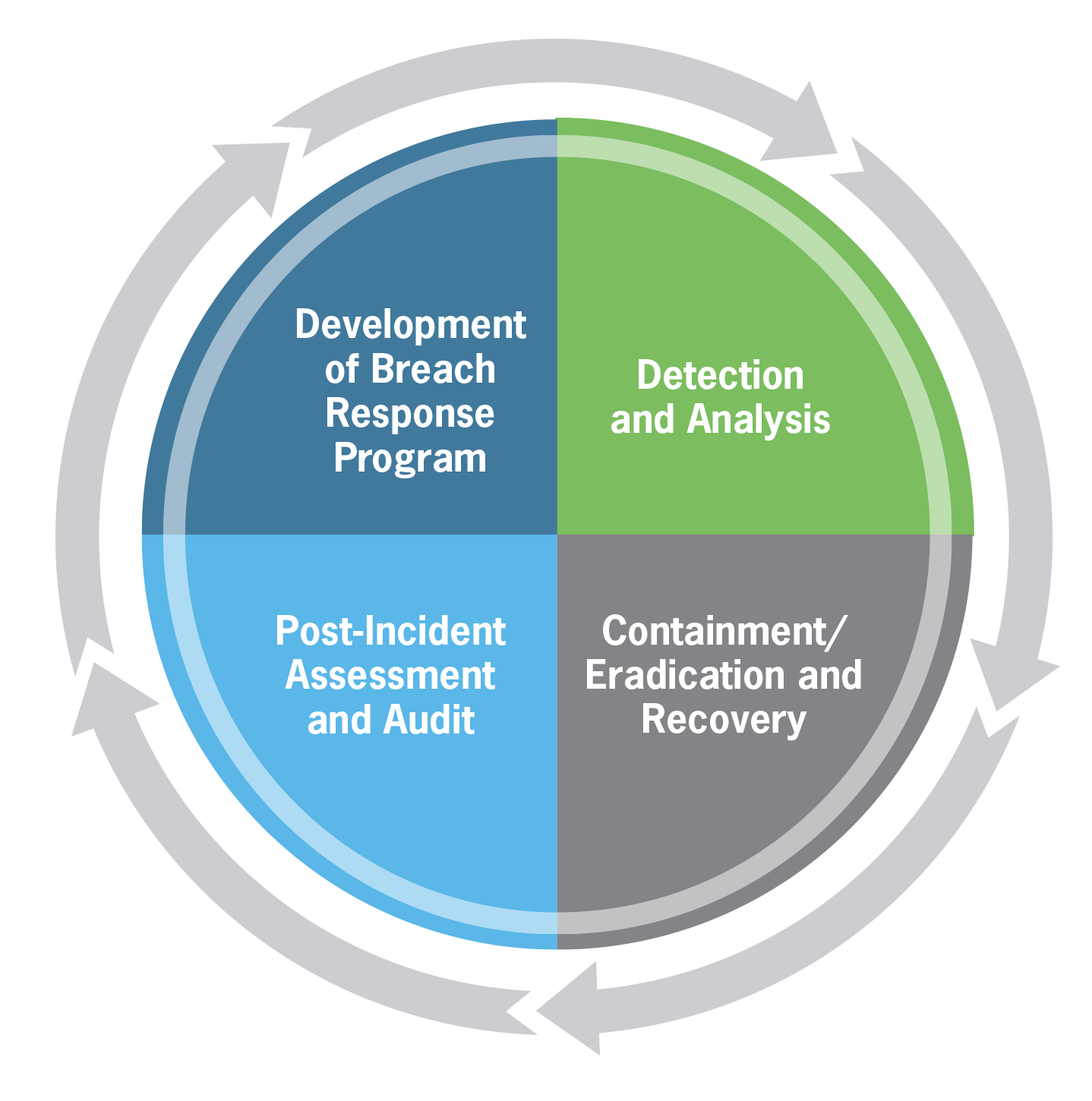
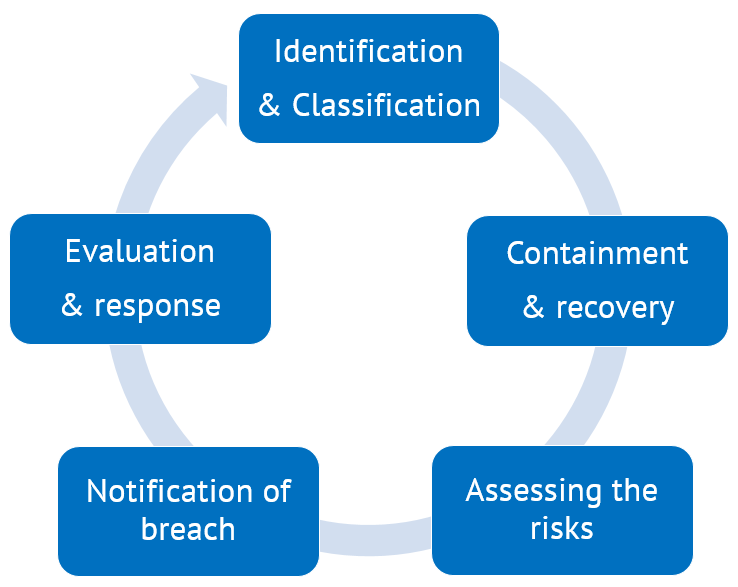
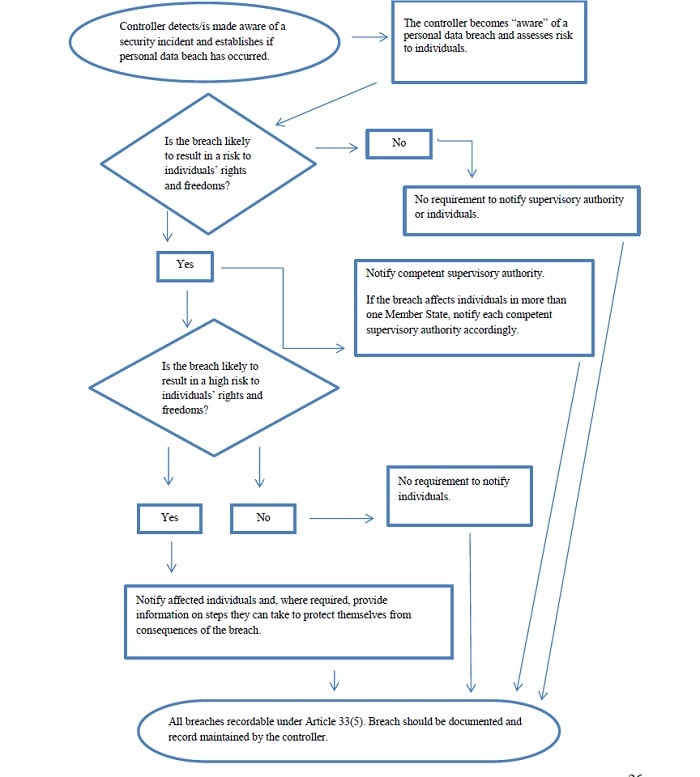
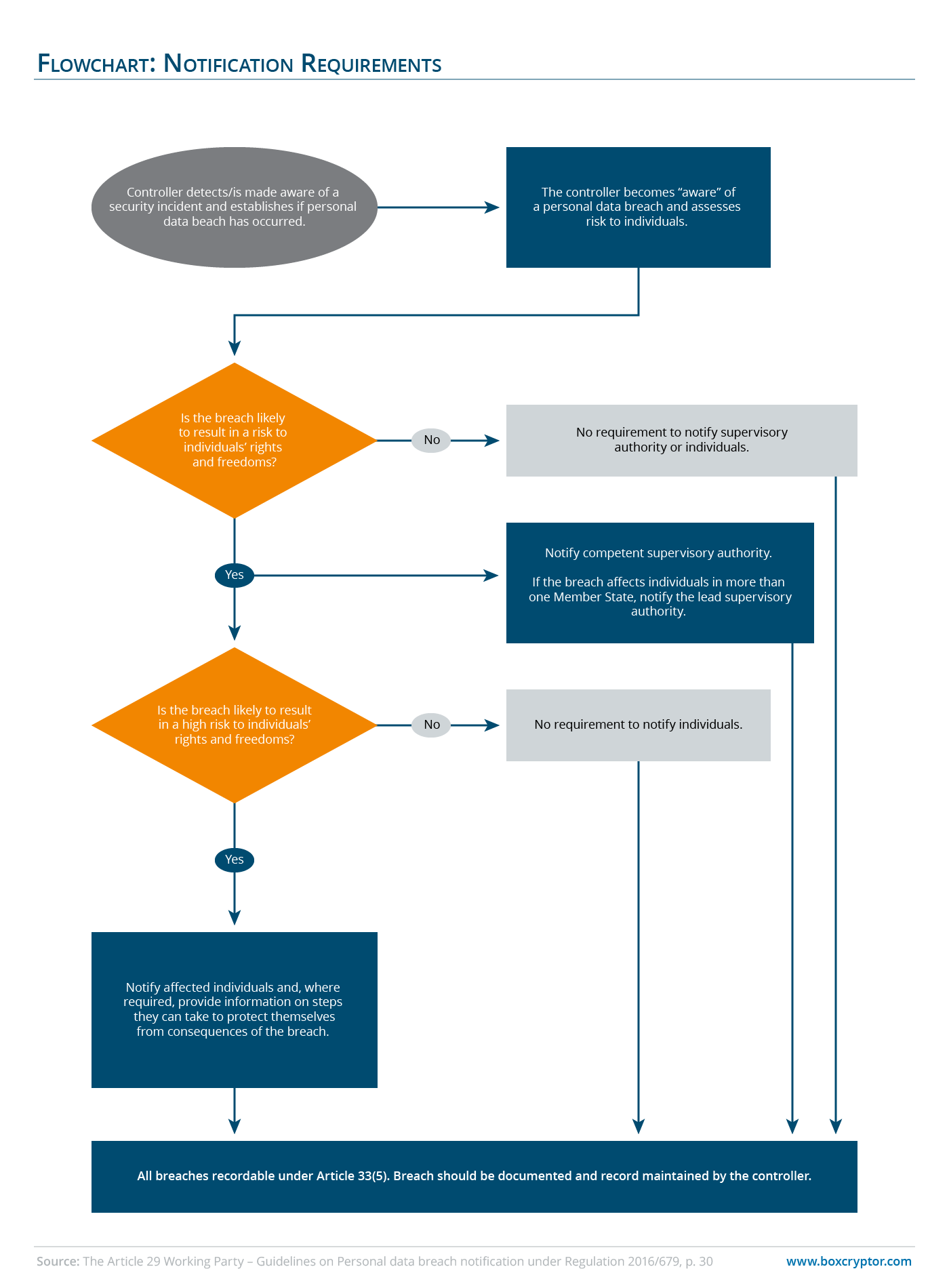
GESTIONE DEL DATA BREACH Procedura da applicare in caso di violazione di dati personali (artt. 33 e 34 GDPR) Versione Data Appro
1 Allegato 7 - Procedura data breach Linee guida per la gestione delle violazioni di dati personali e la loro eventuale comunica