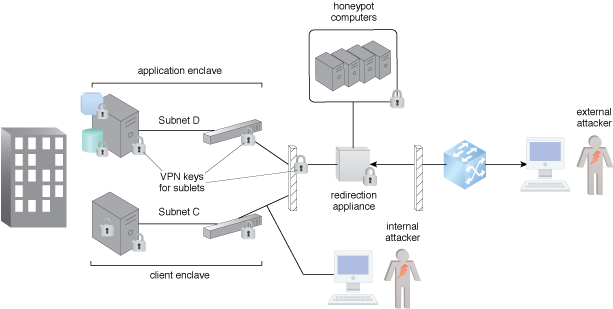
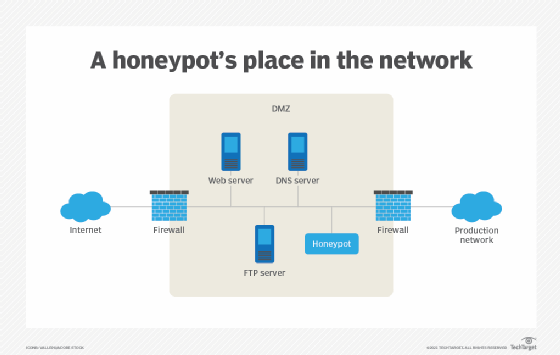
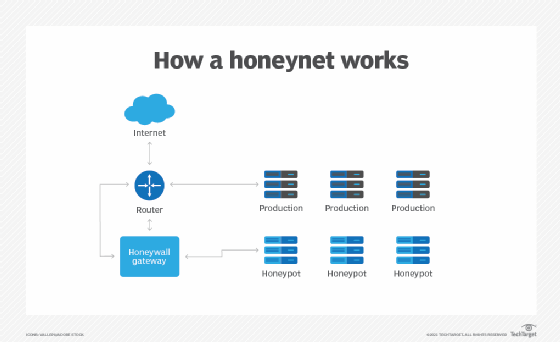
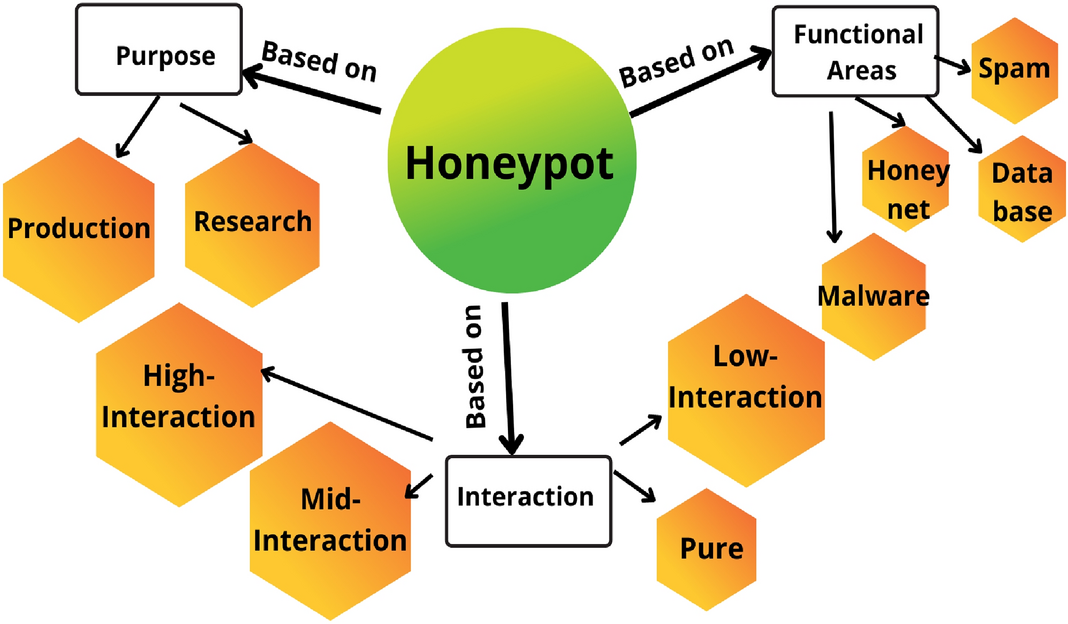
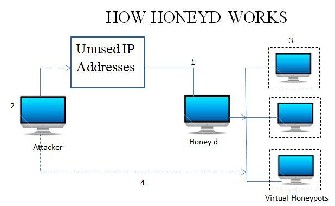
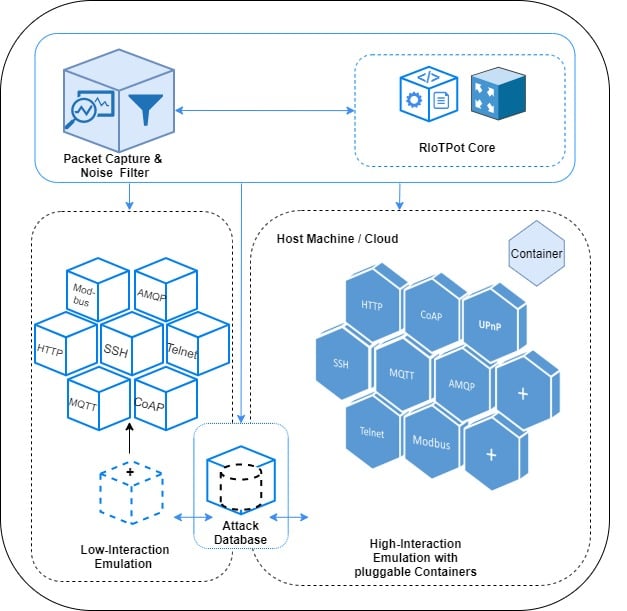
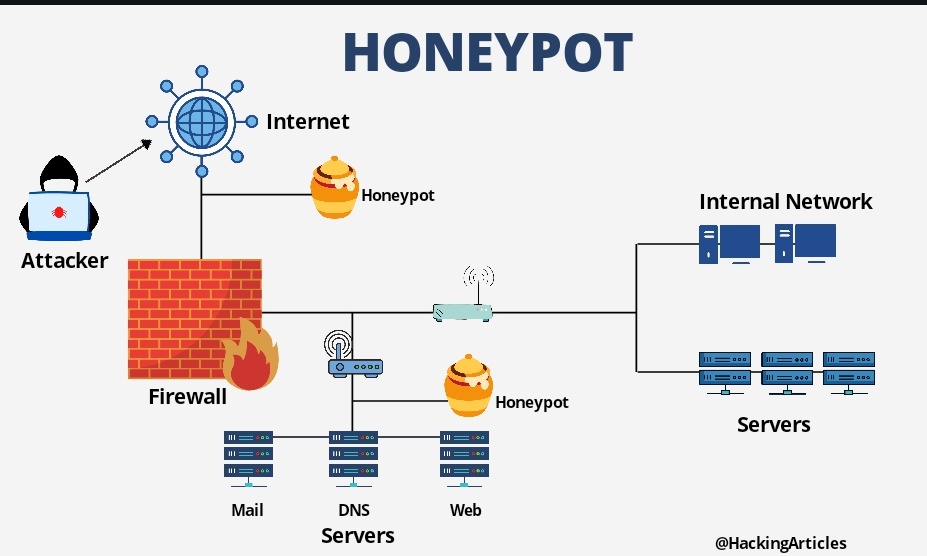
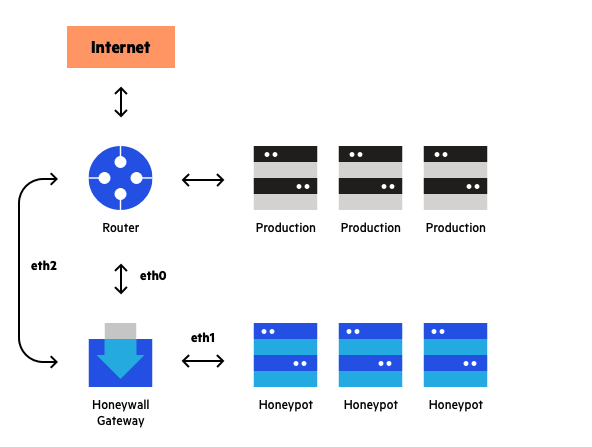
The operation of inter-AS honeypot back-propagation at the start of,... | Download Scientific Diagram

Operating mechanism of honeypot coupled machine learning model in smart... | Download Scientific Diagram
![PDF] D-FRI-Honeypot: A Secure Sting Operation for Hacking the Hackers Using Dynamic Fuzzy Rule Interpolation | Semantic Scholar PDF] D-FRI-Honeypot: A Secure Sting Operation for Hacking the Hackers Using Dynamic Fuzzy Rule Interpolation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/35d325255513b0b579fceaa2f3fe86fe6334045f/9-Figure10-1.png)
PDF] D-FRI-Honeypot: A Secure Sting Operation for Hacking the Hackers Using Dynamic Fuzzy Rule Interpolation | Semantic Scholar