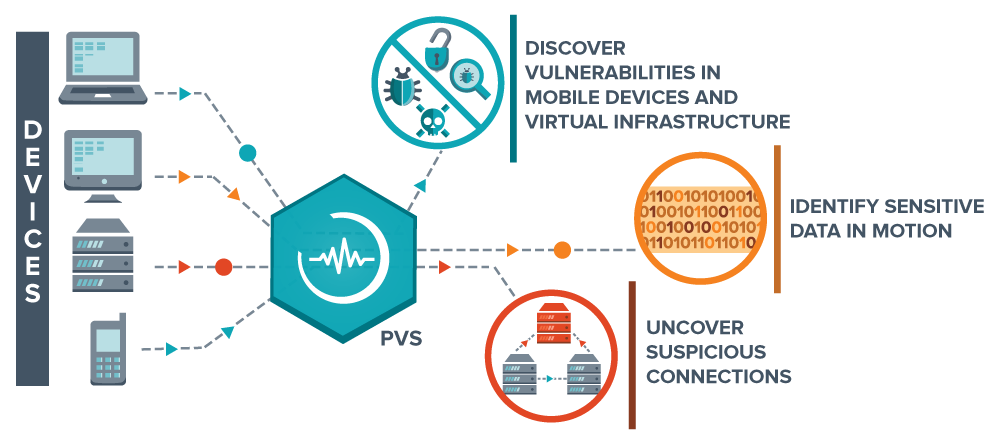
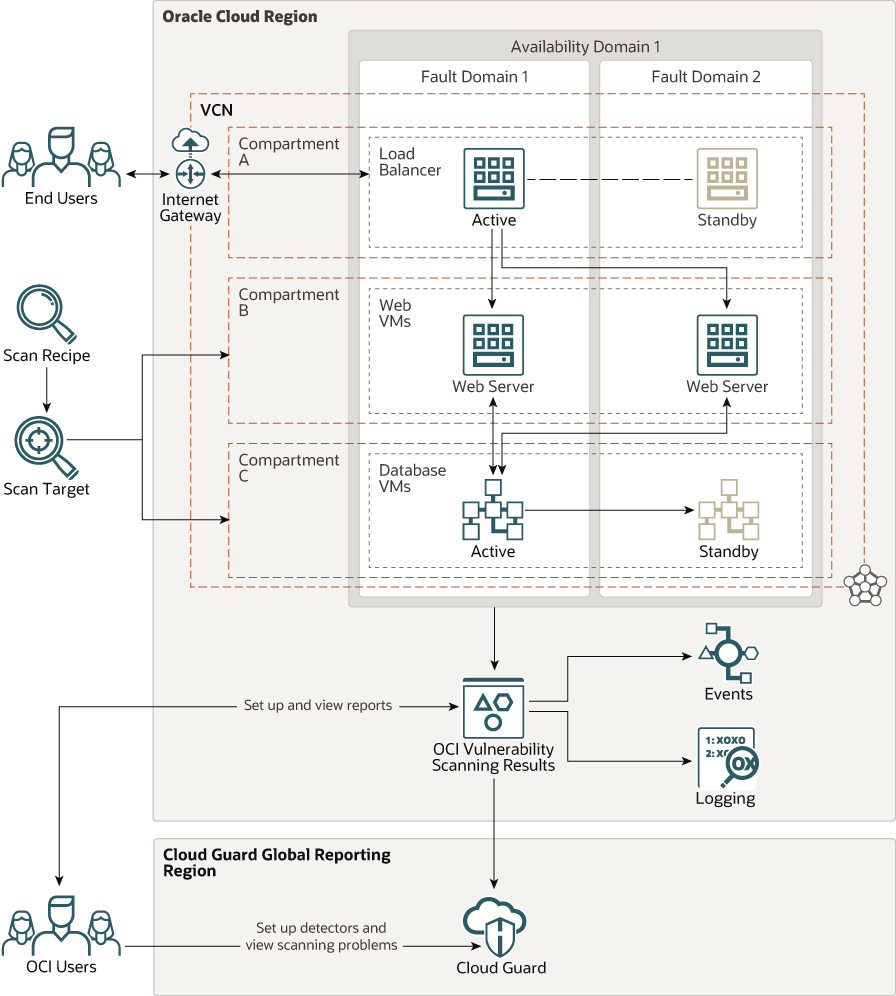
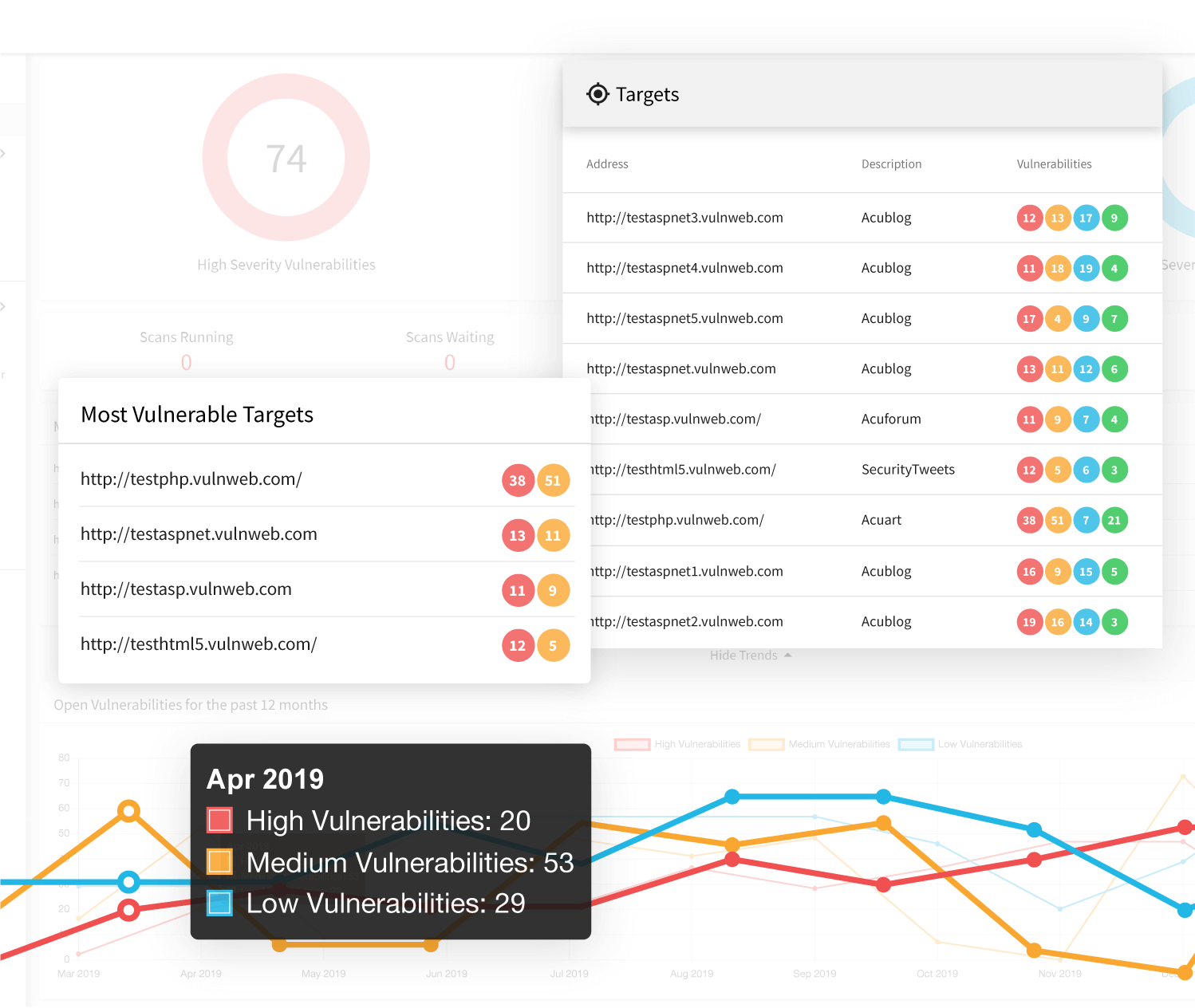
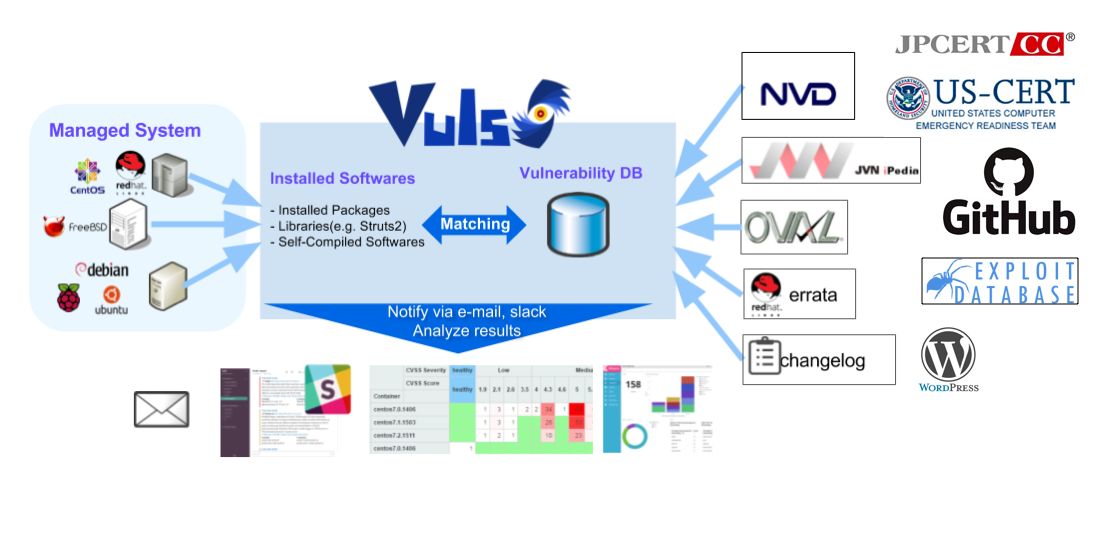
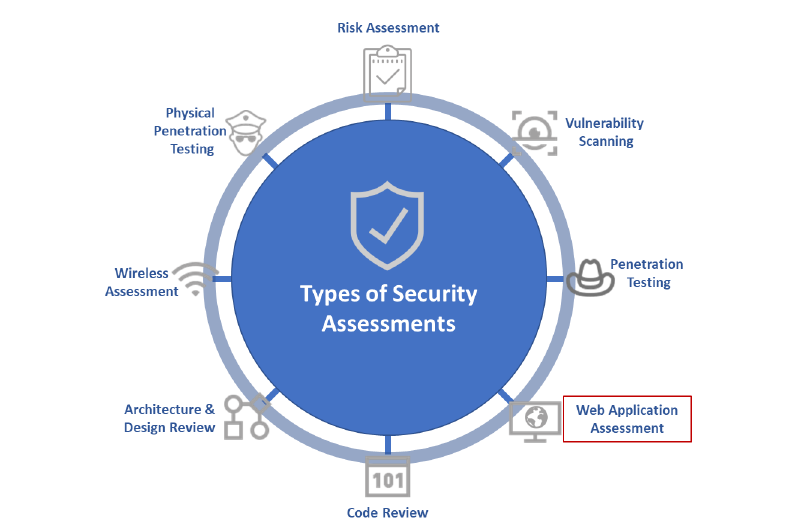
A guide to implement effective cloud vulnerability scanning | nasscom | The Official Community of Indian IT Industry

Guard against security vulnerabilities in your software supply chain with Container Registry vulnerability scanning | Google Cloud Blog
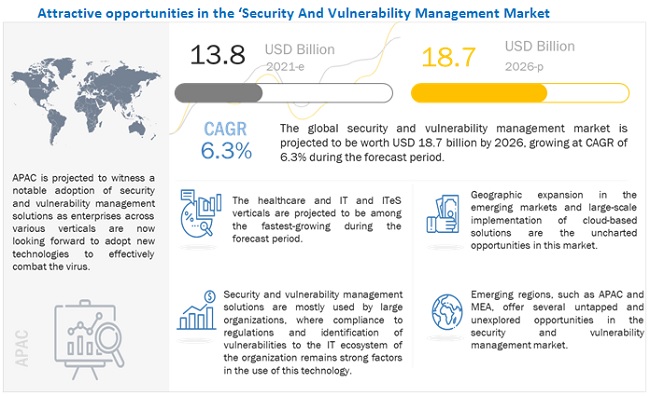
Security and Vulnerability Management Market Size, Share and Global Market Forecast to 2026 | MarketsandMarkets
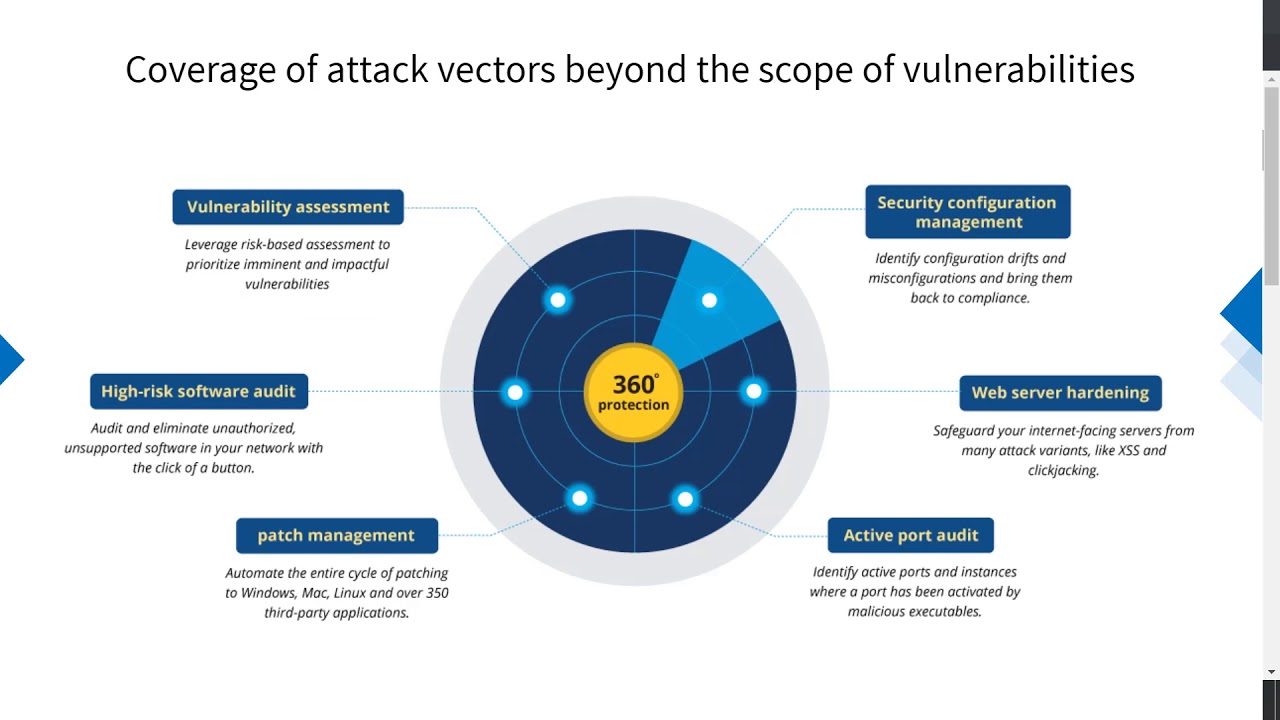
Vulnerability Scanner | Vulnerability Scanning Tools & Software - ManageEngine Vulnerability Manager Plus
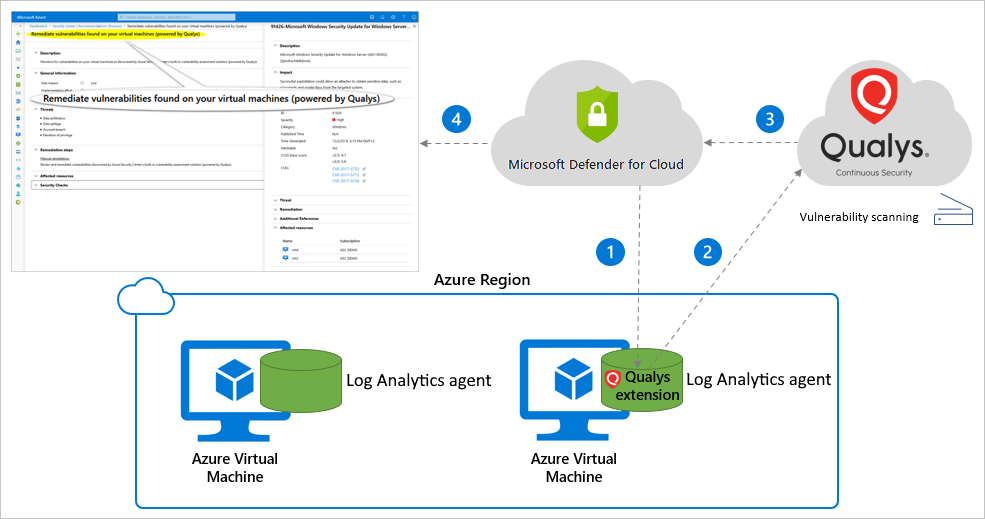
Defender for Cloud's integrated vulnerability assessment solution for Azure, hybrid, and multicloud machines | Microsoft Learn